Retail Company Proactively Safeguards Sensitive Data from Unauthorized Environments Using X1 Distributed Discovery
Summary
A large U.S.-based retail company known for its rapidly increasing revenue from online sales, required a reliable software solution to help ensure its customers' Personally Identifiable Information (PII) was not being stored in unauthorized locations, such as on certain company networks or employee machines, even on a temporary basis. The firm needed a means to proactively search the network, sometimes on a moment's notice, to ensure employees were following the company's strict procedures safeguarding their environment of any PII exposure. They used X1 Distributed Discovery to search, locate and delete sensitive customer information across dozens of offices, residing in unauthorized locations, all from a central location. X1 Distributed Discovery:
- Searched and identified personal information across desktops, laptops and servers days-faster than competitive solutions
- Identified PII instantly within individual email messages stored in PST containers, which was impossible to reach with previous solution without first collecting the data
- Saved the audit and compliance teams thousands of hours
Challenge
This leading retail company needed a faster and more comprehensive approach than their current solution for accessing, analyzing and making quick decisions on sensitive information when found in places it just shouldn't be. The compliance and data audit teams needed the ability to quickly search and react on a moment's notice when dealing with PII such as credit card numbers or other personal information. They felt their current solution and process was too laborious, resource intensive and created a huge disruption to the employees, not to mention impossible to scale to the company's growth.
The firm often struggled with PST files during audits and viewed them as data risk but up to this point, no other technology could open entire PST containers easily and quickly in-place where they resided. They attempted to mandate a “No PST Rule” and were often forced to delete the PSTs when they were found, creating angst and frustration from its employees who regularly referenced old email communications in their day-to-day work. As with many companies, this retail firm struggled with its employees not adhering to the set retention policies. Becoming frustrated with the repeated internal audits, employees started creating PST files and actually hiding them in the cloud when notified of an audit, out of fear of data being remediated by IT without notice. These issues created obvious blind spots and a lack of confidence for audit teams and ultimately risk and exposure to the company.
Managing office and store locations all over the U.S. with employees also working remotely, the firm was also challenged with having data stored in multiple structures and repositories such as desktops, laptops, file servers, cloud repositories, and other enterprise data sources, but needed a way to quickly search it all and bring back instantaneous results. They evaluated technologies that could thoroughly identify data “in the wild” however these technologies first needed to “collect” the data to a central location which would take days or weeks to complete before they could even begin searching against the data.
The manual collection effort with these other technologies still involved manually saving data off of desktops onto mobile storage or sometimes asking end-users to mail in their laptops, creating days of downtime for employees, disruption to their work and frustrations across the board. And in other cases, IT teams spent days or weeks simply managing employee communications and manually creating and tracking the audit trails. This was just not possible to do with a large company and more often than not unauthorized data was just being missed.
Solution
The retail firm turned to X1 to address these challenges. After a brief proof of concept, they immediately recognized X1 Distributed Discovery's unique ability to access, analyze and act upon vast amounts of data very quickly. Specifically, with the index located at the end-node, and distributed across the enterprise, their data could be searched from a central location, in minutes instead of days or weeks. And unlike the other technologies they evaluated, the data did not have to be collected back to a central location before it was searched and manipulated, vastly speeding up the process of accessing the targeted data.
On a moment's notice, the compliance and audit teams could run targeted searches on machines, instantly bringing back results letting them know which users have which types of data and how much data is stored.
The following illustration shows the user experience of an IT/data audit team's results after conducting a keyterm search with X1 Distributed Discovery:
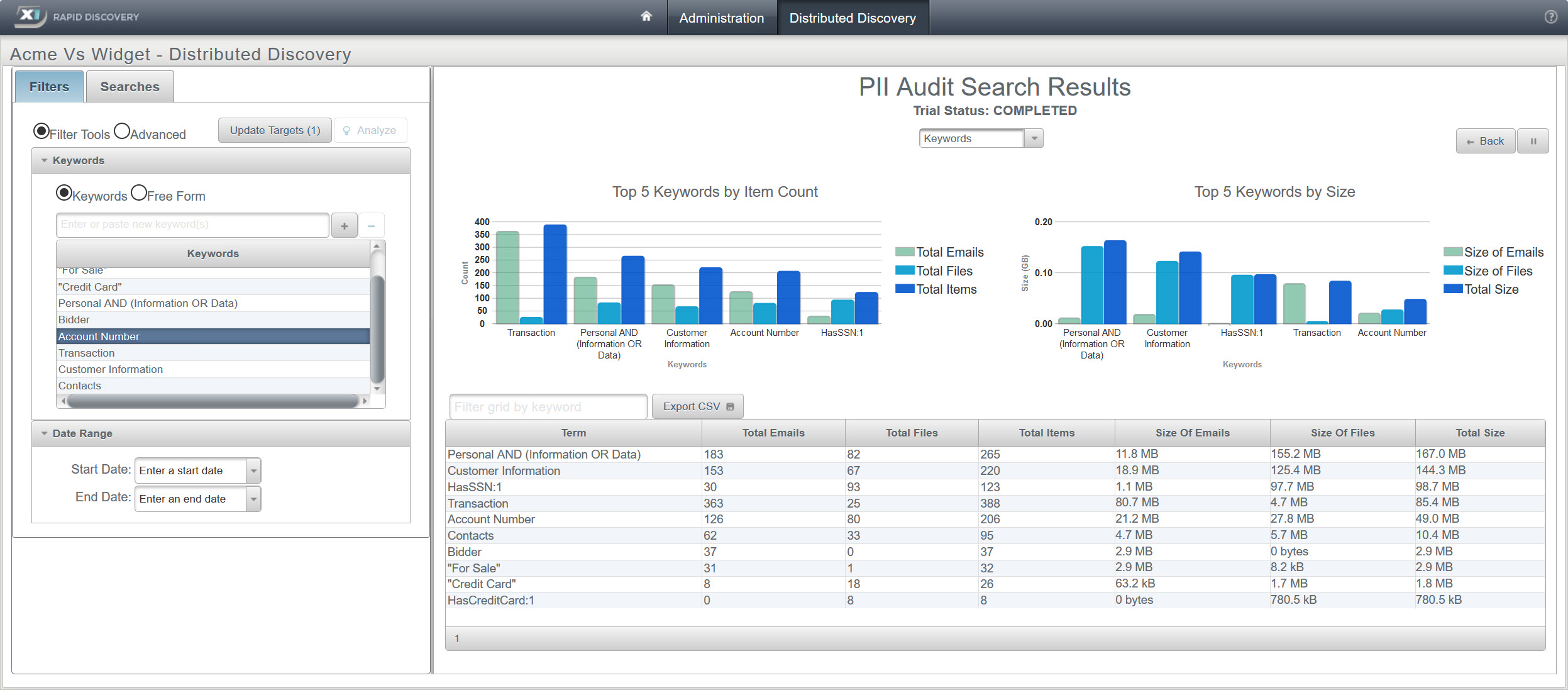
While the other technologies instantly searched the metadata of files, with X1 Distributed Discovery, IT and data compliance teams gained immediate insight into their data by also searching the content of files, emails and attachments in addition to the metadata, empowering fundamentally faster decisions and resolutions. Leveraging X1 Distributed Discovery, the search and remediation of individual email messages directly on the end-user's machine became possible without the laborious and time-consuming transfer of the entire PST email container or requiring the deletion of the entire container file. X1 Distributed Discovery eliminated the need to transfer entire email containers such as PSTs by allowing processing or remediation of individual messages in place on an end-user's computer.
Results
Upon implementation by IT of the enterprise-wide solution, the data audit and compliance teams took turns testing and running search terms on up to 2,000 targeted machines for payment card information and other personally identifiable information relevant to their ongoing audits. Within minutes, these results were completed and displayed as statistics, identifying critical information such item count, quantity and location for each hit (see Figure 1 for example of the results). The team was immediately able to identify 3 sensitive information in unauthorized locations and notify the users immediately with a planned course of action.
The firm was ecstatic to see for the first time ever, they could easily review, process or remediate individual messages alongside all other email messages and never need to transfer entire PST containers again. This feature alone saved thousands of hours for the audit and compliance teams as well as something that would positively impact company morale, no longer fearing chunks of data within PST files would be deleted without notice.